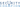
An example of real phishing, when an attacker sends a phishing link in an MSG file.
An example of real phishing, when an attacker pretends that he has already communicated with another employee in our company and is now writing to us.
An example of real phishing, when an attacker pretends that links to files located on Google Drive are attached to an email. After clicking on the links, the employee gets to the phishing site.
An example of real phishing, when an attacker simulates an attachment in an email using images placed in the body of the email.
An example of real phishing, when an attacker sends a link in the form of an IP address so that the user does not understand which site he will get to after clicking.
An example of real phishing when an attacker uses a legitimate website microsoft.com to carry out a phishing attack. Such links are the most dangerous, because an employee may not check which site he enters his password on after clicking on the link.
An example of real phishing, when an attacker's site automatically adjusts to the domain used in an employee's email. Please note that the link in the email leads to google.com
An example of a real attack is when an attacker sends a file in which the contents are not visible. In order to see it, the user is given instructions, after which the computer is infected with a virus.
An example of real phishing is when an attacker sends an empty email and attaches a phishing HTML file in an attachment.
An example of real phishing, when an attacker gives a phishing link not in an email, but in an attached PDF file.